Overview
Welcome to the FAQ section. Here you will find all questions and answers about the services. If you have further questions, please contact our support.
Frequently Asked Questions: Virus Protection
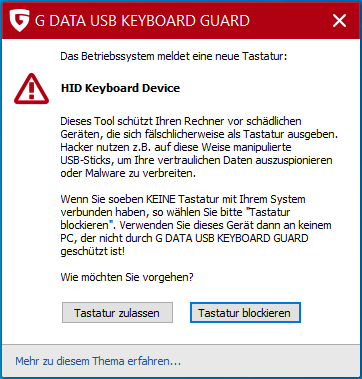
USB devices impersonating a keyboard can be used to attack the system (e.g. in the form of a Rubber Ducky). Therefore, G DATA Security Client warns you when connecting new USB devices with keyboard functionality. If you have indeed connected a keyboard or mouse with a USB dongle, select "Allow keyboard" and then enter the numerical code provided. If the warning message appears when connecting another USB device such as a USB stick, please click "Block keyboard". In this case, please contact your IT contact person.
G DATA offers the option of submitting both erroneously recognized files (so-called false positives) and erroneously unrecognized files (false negatives) to G DATA for review via a web form. After a corresponding check, G DATA will then adjust the detection files accordingly so that the affected files are correctly evaluated in future.
You can find the web form at https://submit.gdatasoftware.com/privacy?lang=de
Please note: Files containing personal data or other sensitive information should not be passed on to G DATA.
Information on malware can be found at RUS-CERT.
Common ways malware spreads include email attachments, links in emails, downloads of software from rogue sources, drive-by downloads when browsing the web, and lateral movement (i.e., spreading from an infected system to other systems on the network by exploiting vulnerabilities or using compromised credentials). Therefore, you can minimize the risk of infection by being extra vigilant about these issues. Specifically, this means:
- Click on links in emails only if you are sure that the message came from a legitimate sender and it is clear where the link leads.
- Open email attachments only if you are sure that the message came from a legitimate sender and you were expecting the attachment.
- If in doubt, always ask the sender by another means (by phone or in person) what type of link or attachment it is.
- If you administer your system yourself: Always keep the operating system and all installed programs up to date.
- When installing new programs, make sure that they come from a trusted source
You can find information on this at the RUS-CERT.